Technology media BleepingComputer reported the emergence of a new type of malware called LameHug, which exploits the open-source Qwen2.5-Coder-32B-Instruct large language model from Alibaba to steal data from Windows 10 and Windows 11 devices. The appearance of this malware marks a new stage in the abuse of AI technology by criminals.
The uniqueness of LameHug lies in its use of a large language model to generate attack instructions, thereby scraping sensitive data from victims' devices. According to a report from CERT-UA (Ukrainian National Cybersecurity Incident Response Team), LameHug is written in Python and relies on the Hugging Face API to interact with the Qwen LLM. The malicious software dynamically generates instructions for stealing data through specific prompts.
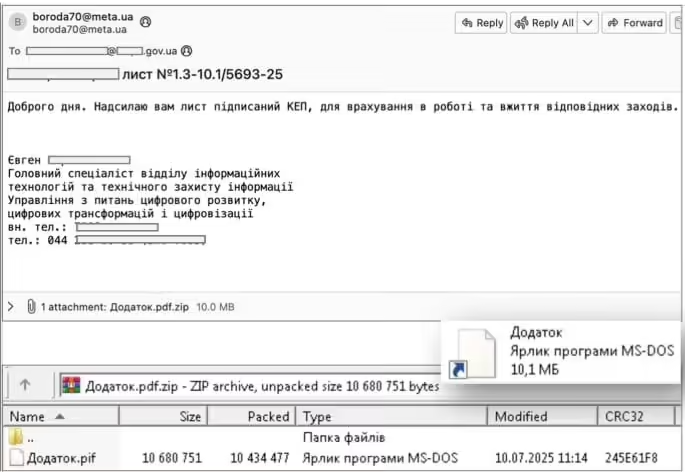
LameHug spreads via malicious emails, usually containing a ZIP file that includes a loader for LameHug. CERT-UA has identified at least three different variants, including files named "Attachment.pif", "AI_generator_uncensored_Canvas_PRO_v0..9.exe", and "image.py". In the specific attack process, LameHug executes system reconnaissance and data theft commands, which are all dynamically generated through prompts.
The generated commands are mainly used to collect system information and save it to a text file (info.txt). It searches for sensitive files in key Windows directories (such as documents, desktop, and downloads) and sends this data to attackers via SFTP or HTTP POST requests. The emergence of this AI-powered malicious software may lead to a new type of attack pattern, posing greater challenges to cybersecurity.
As LameHug spreads widely, security experts remind users to be vigilant, update antivirus software and system patches in a timely manner, and handle unfamiliar emails and attachments with caution to prevent such malware from causing harm. For the general public, enhancing cybersecurity awareness is particularly important.
Key points:
🛡️ LameHug is the first publicly recorded AI malware, specifically targeting Windows 10 and Windows 11 devices.
📧 This malware spreads via malicious emails, with multiple variants that use a large language model to generate data theft instructions.
🔒 Experts remind users to enhance their cybersecurity awareness and update antivirus software and system patches in a timely manner.
